Zero Trust has become a widely known term in the world of modern technology. Seeing as remote work is the new norm for many companies across the country, it comes as no surprise that cybersecurity is a top priority. Employees can access important data from just about anywhere they please and enterprise endpoints are no […]
It’s pretty difficult to imagine technology without the use of passwords. From logging into our mobile device apps to checking email, and gaining access to private networks, you’ve no doubt noticed that other security features are becoming more commonplace. While there are a number of common security practices that help increase security – such as […]
As Russia’s war on Ukraine continues to escalate, so does its diplomatic conflict with the United States. A recent alert was released by Five Eyes intelligence alliance – consisting of the UK, Australia, Canada, New Zealand, and the United States – warning of potential cyber-attacks on a number of critical organizations. Government administration and senior […]
The data held by healthcare organizations include highly sensitive medical records and personal data that can become easy targets for cyber-attacks and other security breaches. Medical facilities need to keep these types of information on record in order to be able to provide care and operate their business. However, that fact often leaves healthcare organizations […]
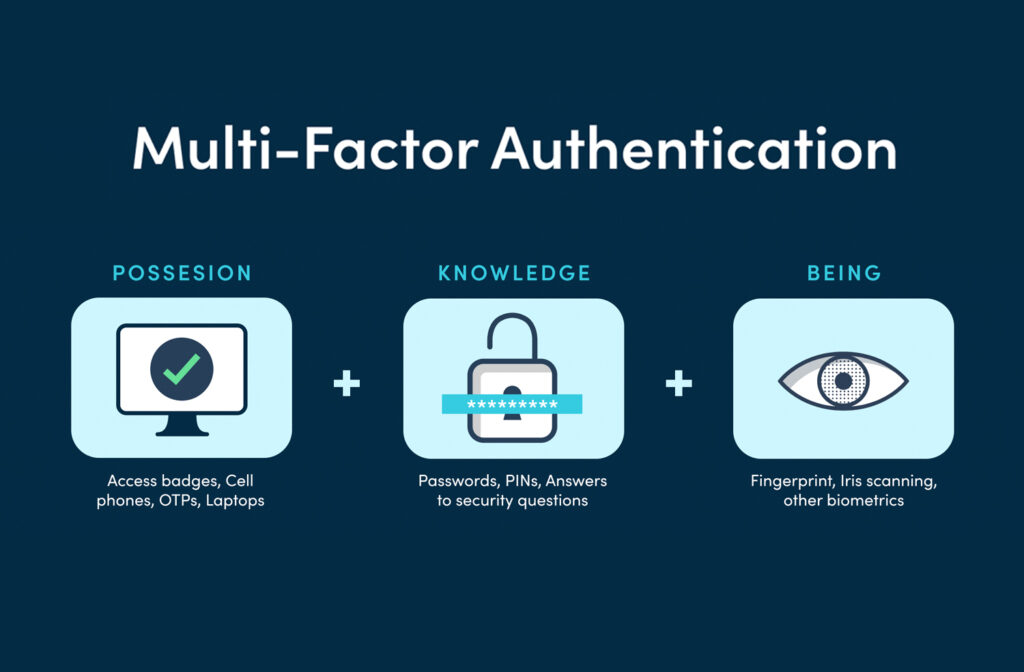
While no system is one hundred percent safe from attempted cyber-attacks, adding multi-factor authentication (MFA) can provide a major line of defense for businesses of all sizes. It is safe to say that every organization has its own set of applications that likely include shared documents, files, folders, videos, customer data, payment transaction records, etc. […]
Since the start of the COVID-19 pandemic in 2020, our society has experienced a rapid digital transformation that does not show any signs of slowing down. While remote work was originally intended to be a temporary response, many businesses have now turned to fully remote and hybrid-working alternatives, which has unfortunately invited a significant increase […]
‘Tis the season to be cautious! Holiday shopping is in full swing, and online shopping is more popular than ever before. Due to the ongoing effects of the pandemic, there are many who are still avoiding stores and buying more online. While this is an extremely convenient alternative, it is important that online shoppers understand […]
Managed IT services can provide numerous benefits across a variety of industries – including accounting firms. Each day, accounting firms are faced with the challenges of remaining productive while also ensuring that their data is secure and the technology they use is up-to-date and operational at all times. If you own an accounting business, it […]
Phishing scams are one of the most common types of cyber-attacks that both business owners and employees are likely to fall victim to. Phishing is known as the fraudulent practice of sending emails designed to trick people into revealing sensitive personal data to the attacker. Whether it is getting access to passwords, credit cards, or […]
It’s no secret that every business, no matter how big or small, needs cybersecurity to protect their private data and information. Furthermore, over the past year businesses have recognized a significant rise in cyber-crime, creating heavy burdens for IT teams that may be lacking the experience and skills in order to respond effectively to serious […]